As curious social animals, humans are more trusting of people than we should be.
Especially when we're dealing with people over the phone, email or via SMS, in the absence of body language.
Australians lost more than $10 million to scammers last year. Follow these easy tips to avoid being conned.
Many of us start a typical day by checking our phones to read emails, social media posts and the weather.
Our phones are trusted devices we use constantly throughout the day to communicate.
But the trust we place in our phones, and the way we interact with the world, also makes it easy for scammers to target us.
Our evolutionary past also makes us susceptible to scams.
Humans are curious social animals, which means we are more trusting than we should be.
That’s especially the case when we’re dealing with people over the phone, email or via SMS, where we don’t have the normal body language cues we would subconsciously process when making decisions.
We are also susceptible to fear and other psychological tools scammers use to create a sense of urgency that tricks us into making irrational decisions and taking action.
Simply being aware that scams are out there is not enough to protect us from them.
We also need to change our behaviour.
Who are these scammers and what do they want?
Scammers come in all shapes and sizes.
Some are individuals, others are gangs.
The more sophisticated scammers are criminal syndicates and foreign governments looking for a way to subvert international sanctions and obtain money through cyber crime.
The motivations of scammers ranges greatly, but can include:
- stealing intellectual property
- tricking you to install malicious software (to steal your data or hold you to ransom)
- stealing your identity so they can pretend to be you and conduct fraud
- tricking you to part with your hard earned cash
- gaining control of your device to steal information at a later date or using your device to attack other people you know.
What techniques are they using?
Scammers are experts at social engineering and use a number of tricks to build rapport, credibility and trust with their targets.
Modifying the caller ID is a simple way to build credibility by making a call or SMS appear to come from an authority like the Australian Tax Office.
The rise of cheap Voice over Internet Protocol (VoIP) providers and other online tools has made it even easier for anyone to exploit the phone systems and “spoof” other numbers.
In the VoIP phone system, the person initiating the call defines the caller ID seen by the receiver.
This is the same for traditional phone systems, however the lower price of VoIP and ease at which the caller ID can be modified without any technical knowledge (via a simple web page) makes it faster and cheaper for scammers to cycle through a number of fake caller IDs in a single day.
It also allows them to move to a new source number or VoIP provider very quickly, making it harder for telcos in Australia to block.
There are legitimate business reasons for allowing the caller ID to be modified, such as when companies operating call centres want all outbound phone calls from their staff to appear to originate from a single “help desk” phone number.
Email spoofing is also common and easy to do.
This is where an attacker forges the email header, making the email look like it originated from a friend, authority or service provider, such as a bank.
A key way to identify a spoofed email is to check the email address itself (the reply field) rather than just relying on the display name in the “from” field.
Most email clients (such as Gmail or Outlook) on desktops or laptops are capable of displaying email headers.
Unfortunately email clients on most smartphones and tablets make it difficult to see the real source and often only show the forged “display name” information.
Phone and email are the two main scam delivery methods. Losses from attempts to gain your personal information rose by more than 61% between 2017 and 2018.
This trend shows no sign of slowing down.
Last year, Australians lost more than $10 million to scammers.
Signs of a scam
Ten common warning signs you are dealing with a scammer include the following:
- being asked for password, PINs or other sensitive information
- being told you are owed a refund
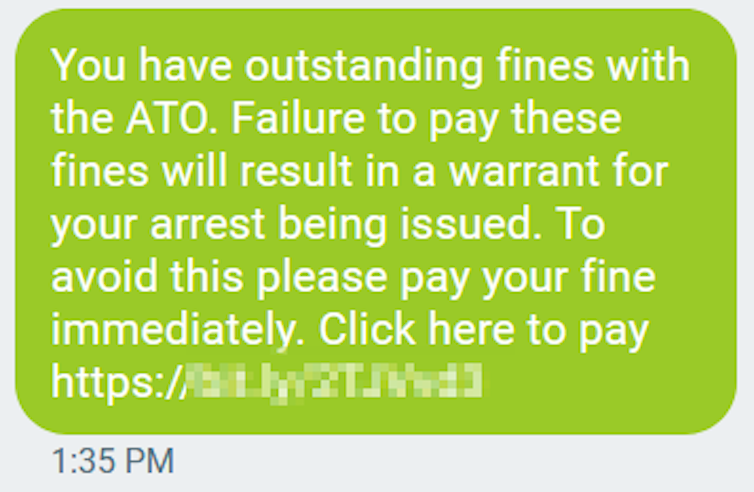
- being told you have unpaid bills, unpaid fines from the police or a government department
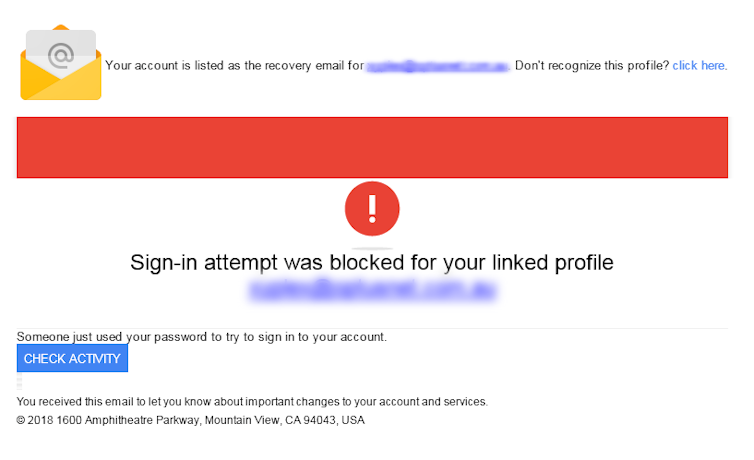
- being notified there is a problem with your email or bank account
- being asked for urgent help
- being congratulated on winning a competition (you didn’t enter)
- being asked you to click on a link or open a document
- being sent you an unexpected invoice to open
- receiving a critical alert message with a link to click
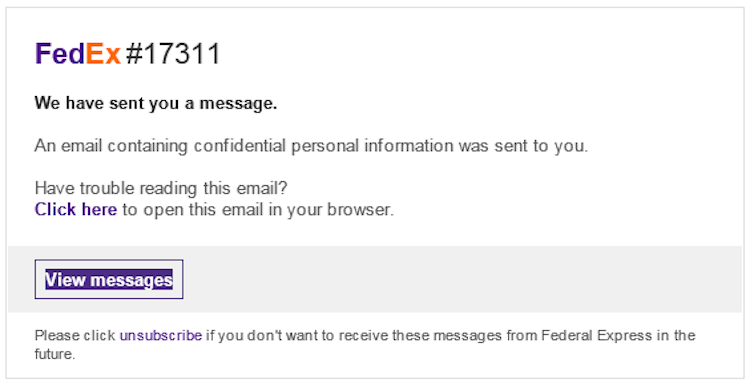
- receiving a tracking number and link for a delivery (you didn’t order).
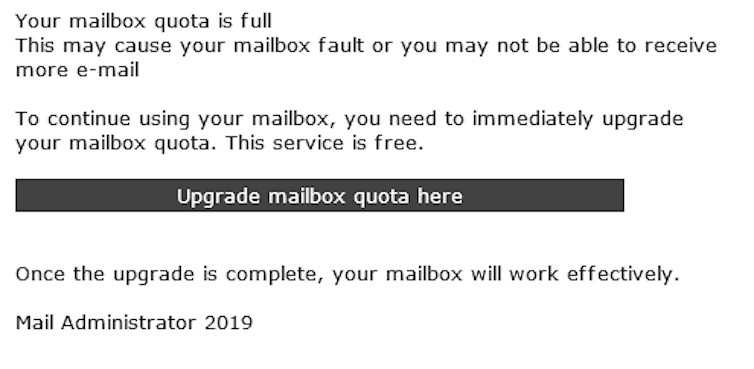
A scam telling you your mail box full is designed to make you click on a link.
Simple tips to avoid being conned
Firstly, don’t click on any links, don’t respond to offers to opt-out or unsubscribe, don’t call return calls from numbers you don’t recognise and, most importantly, don’t give out personal information – even if you think it isn’t important.
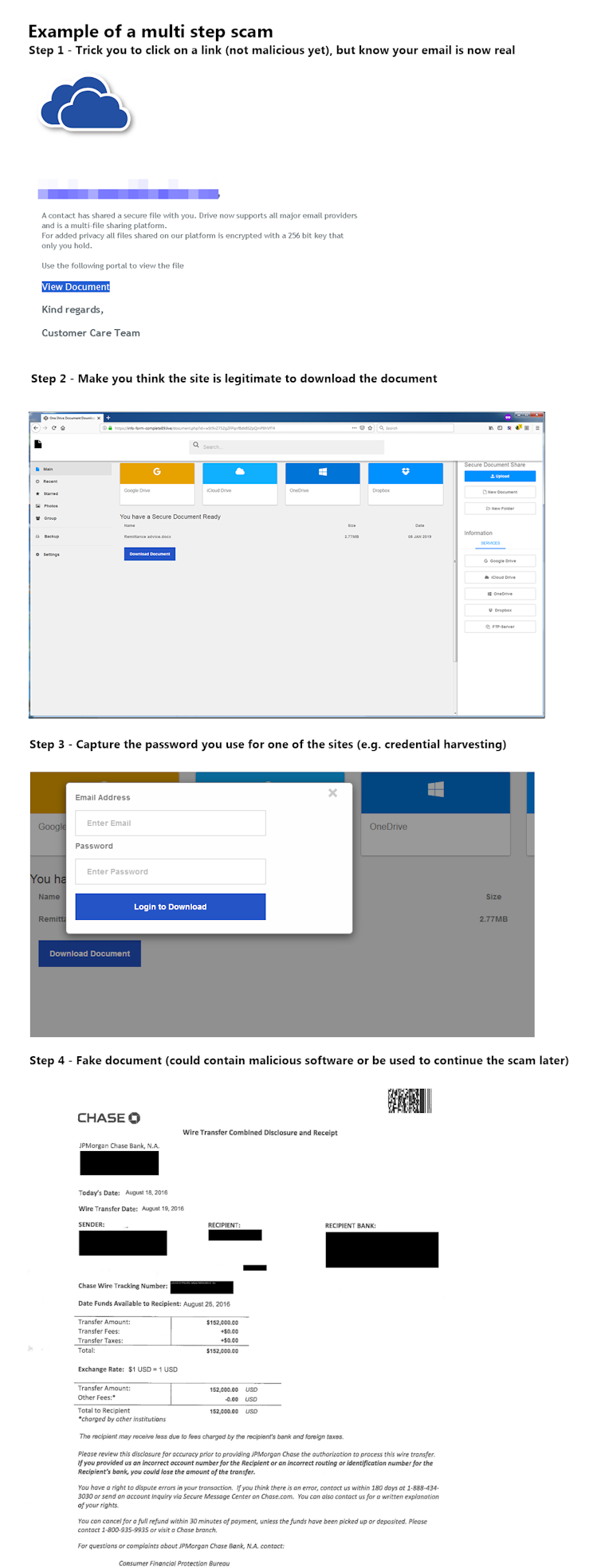
Remember, some scams are multi-step scams.
The best thing you can do is to report the scam and tell your friends and family to be aware of the scam so they can modify their behaviours.
Scams can be reported to various government agencies, such as Scam Watch, the Australian Cybercrime Online Reporting Network (ACORN) and, in some cases, the service provider – for example, the ATO, Telstra, AusPost and the banks.
Author Damien Manuel, Director, Centre for Cyber Security Research & Innovation (CSRI), Deakin University
This article is republished from The Conversation under a Creative Commons license. Read the original article.
NOW READ:
- How to spot a property scam
- Protect yourself from these common investment scams
- Aussies losing $1 million per week to investment scams